After installing T-Mobile’s home internet, many people found that their internal home network was no longer accessible from the outside. You can’t do NAT port forwarding because of the T-Mobile CGNAT, where many clients share a single IPV4 address. And they don’t allow IPV6 delegation either. It is a very different experience compared to the cable, DSL, or FIOS providers. To work around this issue, you can either build a VPN to the VPS in the cloud or use SSH to achieve the same goal. The SSH solution requires fewer resources and takes only 5 minutes to set up.
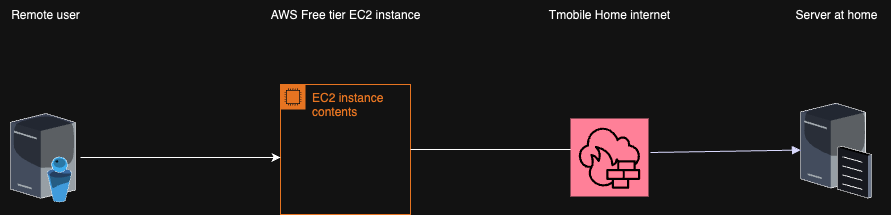
You will need a cloud Linux instance from your favorite provider(AWS,GCP, Azure, etc.). I’m using AWS because the free tier is free for a year. After that, if you are using a micro instance and prepay, the solution costs about $45 for three years or about $1.20 per month.
-
Make sure that you can ssh from the home server to the cloud instance with ssh keys.
-
Update config of your home server, and add port 2222
Port 22 Port 2222 AddressFamily any ListenAddress 0.0.0.0 ListenAddress :: -
If you are using selinux you will need to allow port 2222 for communication
semanage port -a -t ssh_port_t -p tcp 2222
-
Setup persistent ssh connection from the home server to the cloud instance
-
In the example below replace path to the ssh key and the name of the AWS EC2 instance.
$ sudo vim /etc/systemd/system/ssh-tunnel-persistent.service
[Unit]
Description=Persistent SSH Tunnel to AWS on port 22
After=network.target
[Service]
Restart=on-failure
RestartSec=5
ExecStart=/usr/bin/ssh -i /home/afler/.ssh/sshkey.pem -o StrictHostKeyChecking=no -o ServerAliveInterval=60 -o ExitOnForwardFailure=yes -R 2222:localhost:2222 ec2-user@ec2.compute-1.amazonaws.com -tt
[Install]
WantedBy=multi-user.target
$ sudo systemctl daemon-reload
$ sudo systemctl enable ssh-tunnel-persistent.service
$ sudo systemctl start ssh-tunnel-persistent.service
- Check status of the SSH tunnel
$ sudo systemctl status ssh-tunnel-persistent.service
● ssh-tunnel-persistent.service - Persistent SSH Tunnel to AWS on port 22
Loaded: loaded (/etc/systemd/system/ssh-tunnel-persistent.service; enabled; preset: disabled)
Active: active (running) since Thu 2024-07-25 08:31:48 CDT; 2 days ago
Main PID: 66894 (ssh)
Tasks: 1 (limit: 98513)
Memory: 1.1M
CPU: 581ms
CGroup: /system.slice/ssh-tunnel-persistent.service
└─66894 /usr/bin/ssh -i /home/afler/.ssh/sshkey.pem -o StrictHostKeyChecking=no -o ServerAliveInterval=60 -o ExitOnForwardFailure=yes -R 2222:localhost:>
Jul 25 08:31:49 rhlab ssh[66894]: ~\_ ####_ Amazon Linux 2023
Jul 25 08:31:49 rhlab ssh[66894]: ~~ \_#####\
Jul 25 08:31:49 rhlab ssh[66894]: ~~ \###|
Jul 25 08:31:49 rhlab ssh[66894]: ~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023
Jul 25 08:31:49 rhlab ssh[66894]: ~~ V~' '->
Jul 25 08:31:49 rhlab ssh[66894]: ~~~ /
Jul 25 08:31:49 rhlab ssh[66894]: ~~._. _/
Jul 25 08:31:49 rhlab ssh[66894]: _/ _/
Jul 25 08:31:49 rhlab ssh[66894]: _/m/'
Jul 25 08:31:49 rhlab ssh[66894]: Last login: Thu Jul 25 13:25:46 2024 from X.X.X.X
- Once you have a reverse tunnel, you can ssh into the AWS EC2 instance, and ssh to the localhost port 2222. It will bring you to your home server.
ssh -i ~/.ssh/sshkey.pem ec2-user@ec2.compute-1.amazonaws.com
A newer release of "Amazon Linux" is available.
Version 2023.5.20240722:
Run "/usr/bin/dnf check-release-update" for full release and version update info
, #_
~\_ ####_ Amazon Linux 2023
~~ \_#####\
~~ \###|
~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023
~~ V~' '->
~~~ /
~~._. _/
_/ _/
_/m/'
Last login: Sat Jul 27 14:53:15 2024 from 69.293.41.99
[ec2-user@ip-192-35-59-86 ~]$ ssh afler@localhost -p 2222
afler@localhost's password:
Activate the web console with: systemctl enable --now cockpit.socket
Register this system with Red Hat Insights: insights-client --register
Create an account or view all your systems at https://red.ht/insights-dashboard
Last login: Sat Jul 27 17:17:02 2024 from 192.168.0.74
